Know How to Keep a Secret with these Secrets Management Principles
- June 14, 2021
There are basic tenets of good security that all organizations should employ -- things like avoiding hard-wiring passwords into code. Yet, we frequently see well-intentioned organizations run afoul of these basic principles. To help ensure compliance to your organization’s security posture, follow these key secrets management principles.
What is secrets management?
Secrets management refers to all processes that involve provisioning, encrypting, storing, retrieving, and revoking secrets. It uses controls like authentication, authorization, and audit; it utilizes access methods like REST APIs, command line interfaces and UI based consoles.Some examples of secrets:
• API Tokens
• Database user ID and password
• Certificates
• Access and secret keys
• RSA key pairs
• Encryption keys
What is the business value of a secrets management solution?
Cyber risk management requires controls that protect unauthorized access to corporate intelligence -- like data thefts and breaches. While threats are generally perceived as originating from outside the company, there are significant threats from insiders. The 2020 Cost of Insider Threats Global Report study from Ponemon Institute finds that the number of insider threats grew 47%, from 2018 to 2020, the resulting costs to the business grew 31% in this same time.In addition, vendor software and service supply chains are also an emerging attack vector. For example, the recent Solar Winds breach was a supply chain attack where the perpetrators infiltrated a software update, injecting a discrete malicious code as a backdoor thereby gaining access to hundreds of systems. And Target suffered a data breach due to bad actors stealing credentials from its HVAC vendor.
The cost of a data breach runs into the millions of dollars. As a result, part of the goal of many regulations is to help organizations avoid these costs – while saving consumers from having their personal information stolen. Often, these various compliance and assessments (including HIPAA, PCI-DSS, GDPR, and NIST 800-53) require enterprises to implement controls with regard to managing secrets. Hence, implementing a solution to manage secrets has become a standard in cloud native application development.
Secrets management: key principles
For effective secrets management, there are several key principles we recommend organizations follow. Specifically:
- Visible only to the application that owns it
- Restricting visibility of secrets to the application that owns it will eliminate misuse. For example, if database credentials are not access controlled to the scope of application users, they can be misused.
- Restricting visibility of secrets to the application that owns it will eliminate misuse. For example, if database credentials are not access controlled to the scope of application users, they can be misused.
- Never hard coded in programs
- Generally, everyone has read-only access to source code. Hence these secrets can be extracted with an intent to misuse.
- Generally, everyone has read-only access to source code. Hence these secrets can be extracted with an intent to misuse.
- Access controlled authentication and authorization policies
- Secrets like any other resources should be controlled through authentication and authorization. Secrets are “crown jewels” and they should be protected with the highest level of safeguards.
- Secrets like any other resources should be controlled through authentication and authorization. Secrets are “crown jewels” and they should be protected with the highest level of safeguards.
- Stored in encrypted state
- Secrets can be in plain-text or encrypted. Generally secret management solutions provide the option to encrypt the secrets at rest. Encryption is needed to protect the data in the event of a data breach.
- Secrets can be in plain-text or encrypted. Generally secret management solutions provide the option to encrypt the secrets at rest. Encryption is needed to protect the data in the event of a data breach.
- Transmitted across encrypted channels
- TLS 2.0 or HTTPS protocols provide encryption-in-transit. These controls are necessary to prevent data leakage due to threats like packet sniffing or man in the middle attacks.
- TLS 2.0 or HTTPS protocols provide encryption-in-transit. These controls are necessary to prevent data leakage due to threats like packet sniffing or man in the middle attacks.
- Changed/rotated at regular intervals
- Rotating secrets mitigates the impacts of theft or misuse
- Rotating secrets mitigates the impacts of theft or misuse
- Usage and access controlled and monitored through audit logs
- Audit logs provides a way to monitor access patterns and analyze data theft or leakages.
- Audit logs provides a way to monitor access patterns and analyze data theft or leakages.
- Revoked when not needed
- Timely revocation of credentials prevents misuse and eliminates data thefts and breaches.
- Timely revocation of credentials prevents misuse and eliminates data thefts and breaches.
- Provisioned and revoked dynamically and automatically
- Automatic provisioning and revocation help in automating secrets management by using API calls, IaC, and CI/CD pipelines for provisioning and management of secrets.
There are many tools and solutions in the secrets management space. The CCNF end user technology radar offers a fairly comprehensive list, including the following — tools by category:
Assess:
• GCP secrets management
• SOPS
Trail:
• Bitnami sealed secrets
• Encrypted repositories
Adopt:
• Hashicorp Vault
• AWS Secrets Manager
• AWS Certificate Manager
• AWS AWS Key Management Service (KMS)
While the feature sets and benefits of each of these solutions varies, HashiCorp Vault serves here as an illustrative example of the key features of a secret management solution.
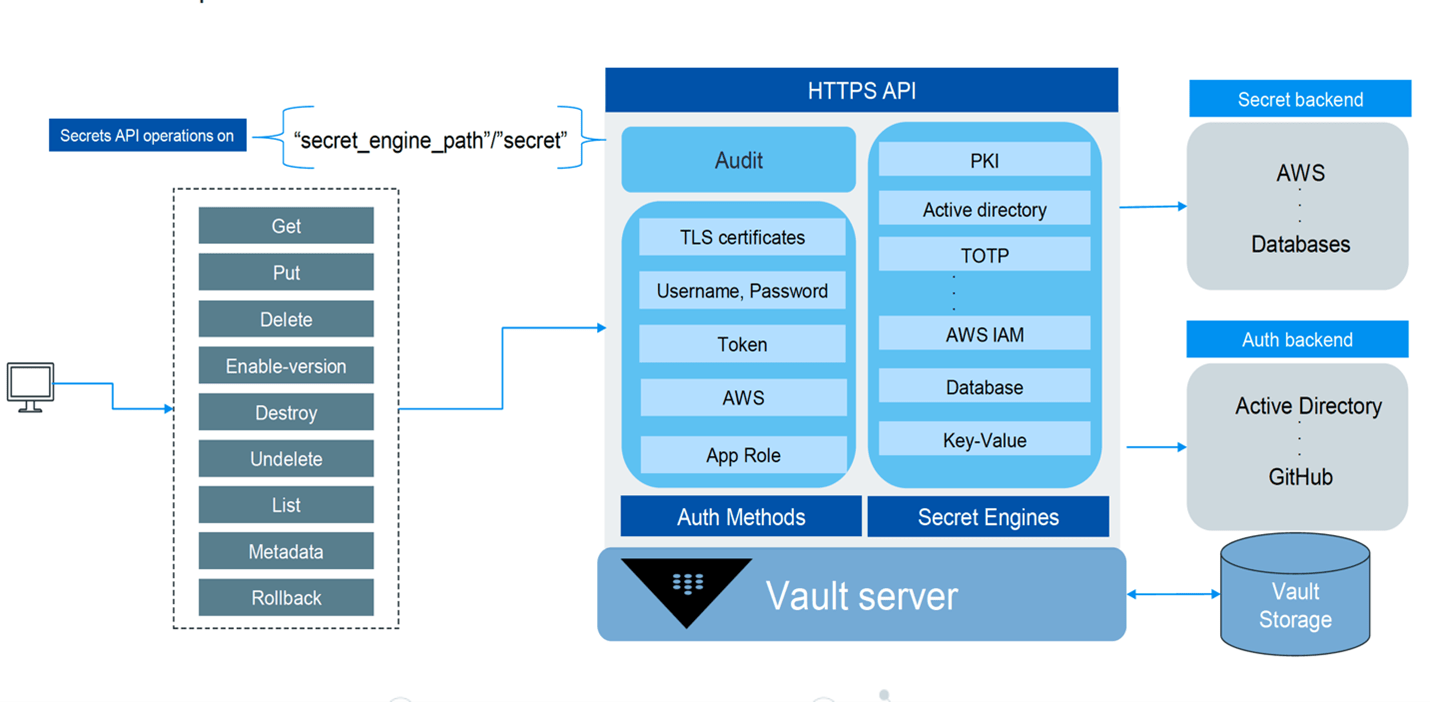
Specifically, HashiCorp Vault users can expect the following features to help them manage secrets:
- HTTPS REST APIs, CLI and UI Console based administration and user access.
- Different authentication methods to control user and programmatic access.
- Authentication can be federated with trusted authentication providers using authentications backends like Active Directory etc.
- Secrets engines provide core functionality for storing, retrieving, provisioning and revoking different types of secrets.
- Different secret engines provide different functionalities. While some simply store and retrieve data, some provide encryption, and others provide functionalities like dynamic provisioning and revocation of credential
- Vault integrates with different trusted secrets backends to provide dynamic provisioning, revocation, and rotation of secrets.
- Data can be persisted into different storage backends including filesystems, object storage, or databases like RDMS or NOSQL.
Effective secrets management grows in importance as your environment becomes more complex. For example, one area where this is heavily used is in the development of cloud native microservices. Developing cloud native microservices involves integration between a myriad of different kinds of services. Authenticated and secure access to these services requires management of secrets like keys, certificates, passwords, and tokens. A secrets management solution provides the necessary backbone infrastructure for operating cloud native microservices.
Beyond microservices, a secrets management solution can be used by end users and administrators to manage secrets; it can be integrated into any application, program, specialized tool, or script, and can be used as part of IaC and CI/CD pipelines. Hence secrets management is an essential technology to consider in modern cloud native application development and maintenance.
Explore more cloud security best practices.
Subscribe to our blog




