Security in AWS with the New Amazon GuardDuty
- January 13, 2018
We’ve recently fielded several inquiries from customers asking about the new Amazon GuardDuty service, its features, and potential fit for their organization. Knowing that their questions may be indicative of a wider interest in the new managed service that monitors and detects malicious or unauthorized behavior across an organization’s AWS infrastructure, we are sharing today our analysis of Amazon GuardDuty.
What is Amazon GuardDuty?
Amazon GuardDuty is a continuous monitoring service that analyzes and processes data sources such as VPC Flow Logs, AWS CloudTrail event logs, and DNS logs. It uses threat intelligence, such as malicious IPs and domains, and machine learning to track any suspicious activity in an AWS account.
Amazon GuardDuty has one master account and can support up to 100 member accounts that are linked to the master account. Note that the master account must invite — and the member accounts must accept the invitation from the master account — in order to link. (The GuardDuty master account should not be confused with other master accounts, like billing.)
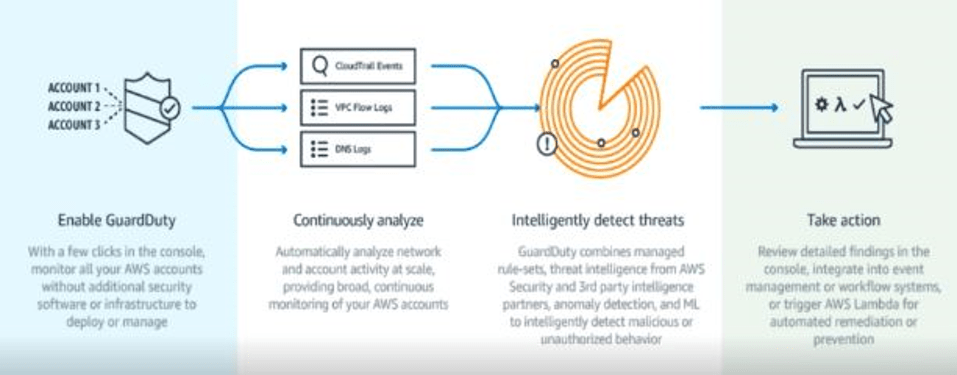
Amazon GuardDuty functionality, courtesy of AWS
Amazon GuardDuty has three primary components:
1. Detector, a unique identifier for the GuardDuty service which is assigned when the master account is initialized.
2. IPSet, a whitelist of IP addresses. The IPSet can be defined as a set or list through a text file or a JSON file.
3. ThreatIntelSet, a blacklist of malicious IP addresses that will be blocked.
Last, Amazon GuardDuty presents findings for accounts monitored. Findings are presented in the form of a report, which as you can see below are categorized as high, medium and low severity. Some examples of how findings are categorized:
- High Severity: A resource completely utilized by a third party, such as a comprised EC2 instance that is continuously sending your information elsewhere, would be labeled a high severity finding.
- Medium Severity: Resources targeted by a TOR network, from where your network packets are being continuously monitored, is an example of a medium severity finding.
- Low Severity: A resource was compromised, and Amazon GuardDuty took action against it such that the malicious activity was halted, would be flagged as a low severity finding.
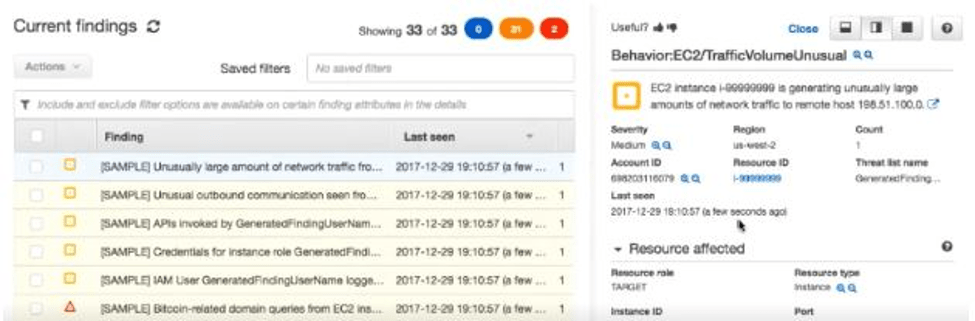
An example finding that Amazon GuardDuty ships with. Note the High, Medium and Low severity findings as reflected by Red, Yellow, and Blue, respectively.
Findings are accessible through the master account and are stored there for 90 days. Past 90 days, operators can archive findings or export them to S3 which we find useful for more strategic, trending analysis.
Taking Action
Depending on the findings, you likely will want to take action. Amazon GuardDuty allows you to automate your threat response. Specifically, Amazon GuardDuty allows you to use HTTPS APIs, CLI tools, and AWS CloudWatch Events to automate security responses. Using CloudWatch Events as an event source, we can trigger a Lambda function that initiates a custom action. For example, if you had a finding that your EC2 instance was attacked, you could configure a CloudTrail event which would have the particular instance ID which would in turn be passed on to another AWS service to drag down the instance.
Our Take:
Importantly, GuardDuty trolls for signs of unusual activity that could be caused by attackers. Previous to GuardDuty, organizations would rely on outside security tools for threat detection and have to analyze each AWS account individually. Now with GuardDuty, operators can analyze threats across accounts, all from the AWS Management Console and without the need for supplemental tools.
Particularly, we like that Amazon GuardDuty:
- Allows operators to easily enable a log group in CloudWatch for GuardDuty. There is no configuration necessary to watch or monitor these logs, you only need to enable these services and GuardDuty takes care of the rest.
- Uses AI-based machine learning algorithms to check the routine behavior of the account to grow its baseline over time.
- Allows operators to easily configure custom events using Lambda to determine which action to take in the event of suspicious activity.
- Supports a variety of event notification services, such as SNS.
- Has a straightforward, easy configuration process for configuring the master account.
- Allows you to upload an existing threat intelligence or whitelist to the service.
- Provides continuous monitoring for threats, providing an ongoing view of your AWS security posture. Amazon GuardDuty is a powerful new inspection tool that streamlines security monitoring, which is always welcome in a multi-layer approach that keeps enterprises secure and compliant.
*This was originally written by Flux7 Inc., which has become Flux7, an NTT DATA Services Company as of December 30, 2019
Subscribe to our blog




